Verified AI summary ◀▼
Set up Okta single sign-on for your Contact Center to streamline user authentication. This involves creating a SAML application in Okta, configuring SAML integration, assigning users, and specifying the identity provider for agent authentication. This setup enhances security and simplifies access management across Amazon Connect and your Contact Center.
You can configure Amazon Connect and Contact Center for SSO with Okta as the SAML-based identity provider. Each requires a SAML application to authenticate. You create the SAML applications in the Okta portal.
The Okta SAML application, along with an AWS Identity and Access Management (IAM) provider, enables federation between Okta and your AWS IAM users.
This article contains the following topics:
Configuring SSO for Amazon Connect
Refer to the AWS guide to configure Amazon Connect SSO with Okta as the identity provider.
Use Service Control Policies (SCPs) to manage user and role permissions in Amazon Connect, protecting important resources and making your system more secure. Refer to the Security best practices for Amazon Connect for more best practices.
The following is an example SCP that you can use to prevent the deletion of the Amazon Connect instance and associated role.
<pre><code class="language-json">
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AmazonConnectRoleDenyDeletion",
"Effect": "Deny",
"Action": [
"iam:DeleteRole"
],
"Resource": [
"arn:aws:iam::*:role/***Amazon Connect user role***"
]
},
{
"Sid": "AmazonConnectInstanceDenyDeletion",
"Effect": "Deny",
"Action": [
"connect:DeleteInstance"
],
"Resource": [
"***Amazon Connect instance ARN***"
]
}
]
}
</pre></code>
Configuring SSO for Contact Center
Configuring SSO for Contact Center includes the following steps:
Step 1: Create a SAML application in Okta
To enable the federation between Okta and your AWS IAM users, create a SAML application in Okta.
To create a SAML application
- Open the Okta developer console.
- In the navigation menu, expand Applications, then click Applications.
- Click Create app integration.
- In the Create a new app integration menu, select SAML 2.0 as the sign-in method.
- Click Next.
Step 2: Configure SAML integration for your Okta application
In this step, you'll configure the SAML integration for your Okta application.
To configure SAML integration
- On the Create SAML integration page, under General settings, enter a name for your app, then click Next.
- Complete the following fields:
- Single sign on URL: https://${yourDomainPrefix}.auth.${region}.amazoncognito.com/saml2/idpresponse
-
Audience URI (SP Entity ID): urn:amazon:cognito:sp:
${yourUserPoolId}
Replace ${yourDomainPrefix}, ${region}, and ${yourUserPoolId} with the values for your user pool.
- Under ATTRIBUTE STATEMENTS (OPTIONAL), add a statement with the
following information:
SAML attribute Name Value http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress user.email. - Leave the other settings as their default values or set them according to your preferences.
- Click Next, then click Finish.
Step 3: Assign users to your application
In this step, you'll assign users to the application you created in step 1.
To assign users to your application
- On the Assignments tab for your Okta app, under Assign, select Assign to People.
- Click Assign next to the user that you want to assign.
- Click Save, then click Go back.
Your user is now assigned.
- Click Done.
Step 4: Specify the identity provider to be used for agent authentication
In this step, you'll add an identity provider to authenticate your agents.
To specify the identity provider
- On the sign on tab for your Okta app, find the identity provider metadata hyperlink, then right-click the hyperlink and copy it.
- Sign in to the AWS account containing the Cognito userpool.
- Navigate to Cognito and open the userpool.
- Click the Sign-in experience tab, then click Add identity
provider.
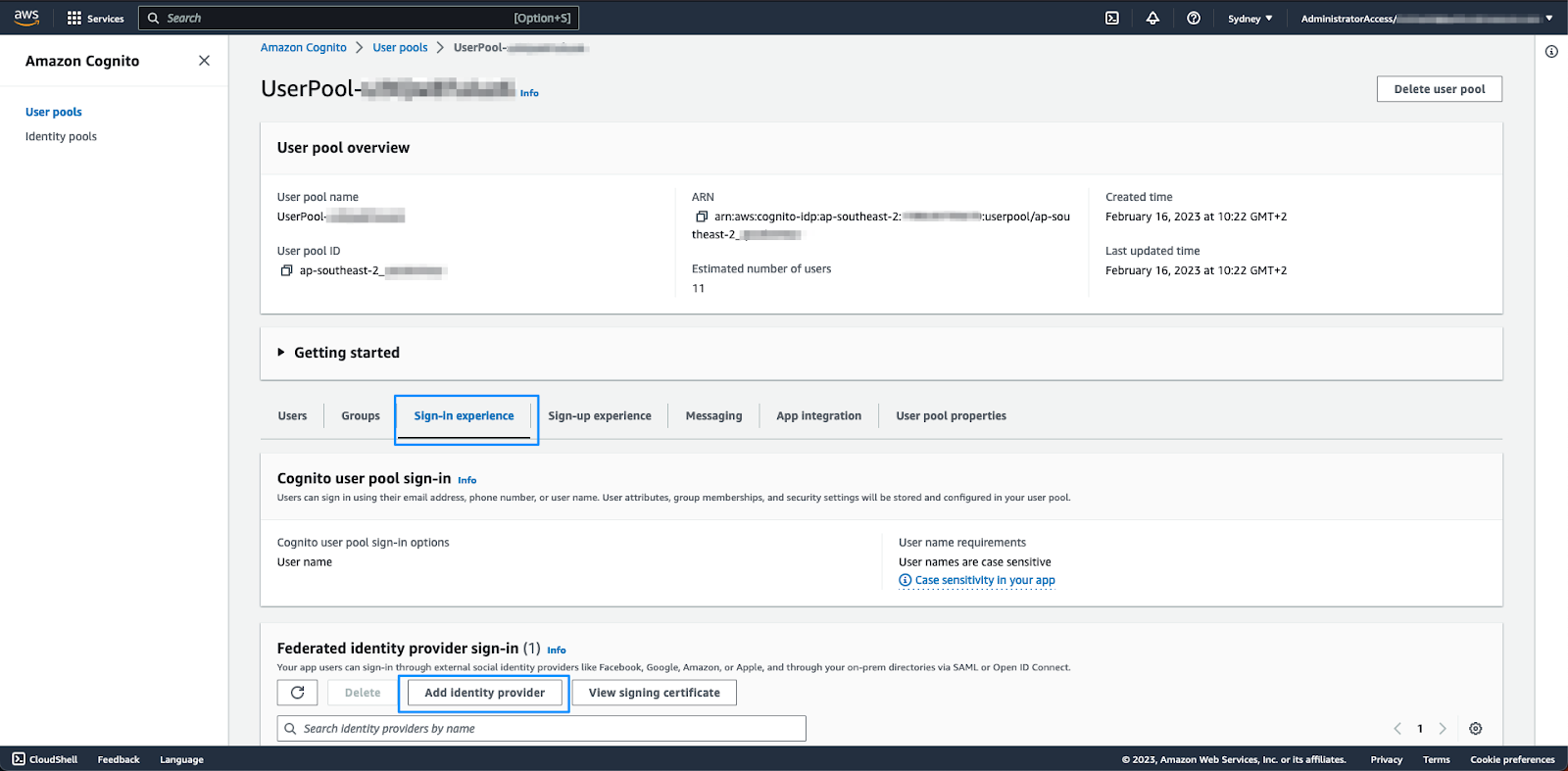
- On the resulting page, select SAML.
- Under Set up SAML federation with this user pool, do the following:
- Provider name: Enter a name for the identity provider without using any spaces in the name.
- Metadata document source: Paste the Metadata URL from the previous step in the metadata endpoint URL field.
- Under Map attributes between your SAML provider and your user pool, set the
following attribute:
User pool attribute SAML attribute email http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress - Click Add identity provider.
At this point the required identity provider has been created. The last step in the Cognito configuration is to specify that the app client must use this identity provider.
- Click the App integration tab, then click app-client at the bottom of the page.
- In the app-client, in the Hosted UI section, click Edit.
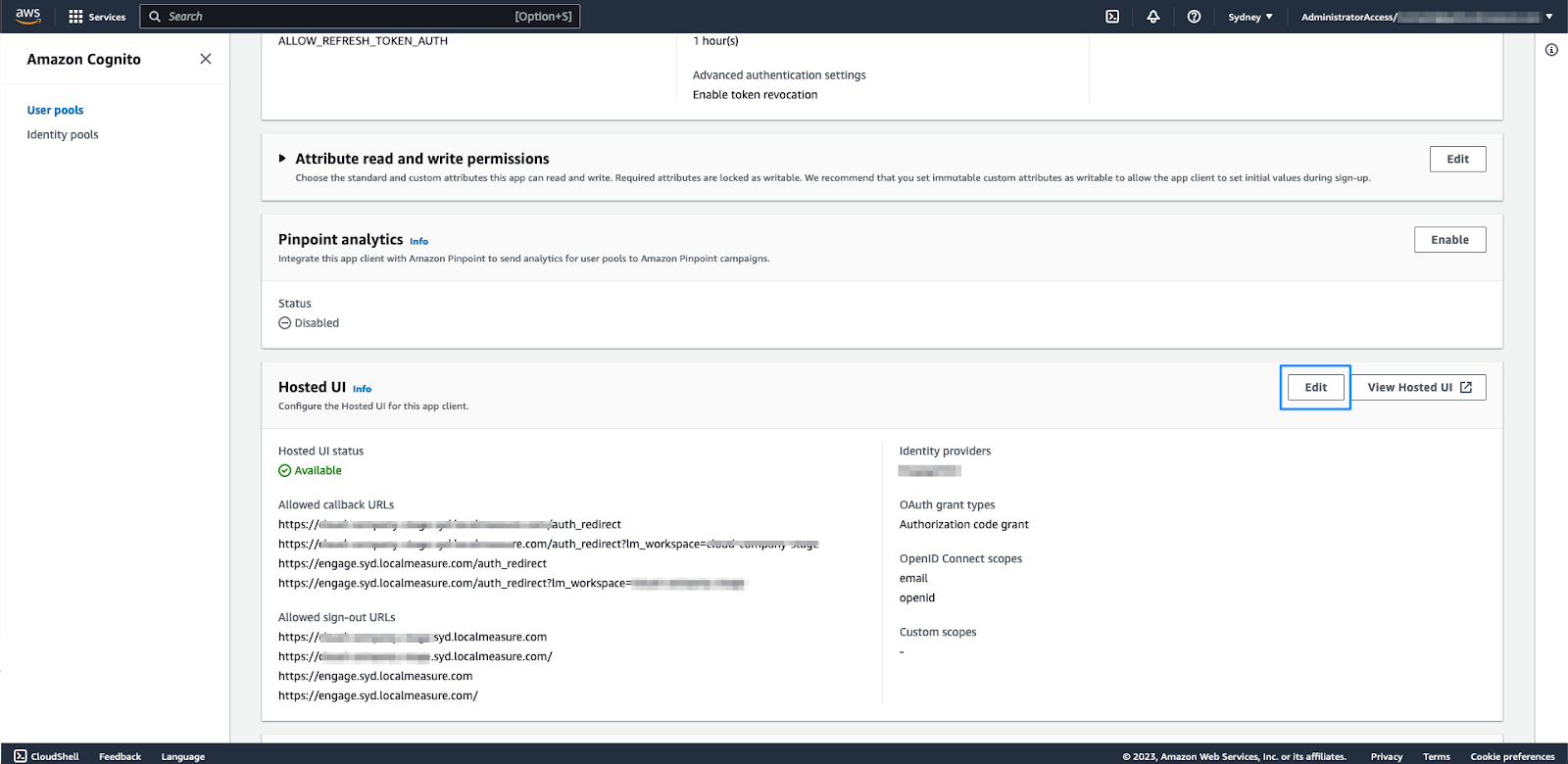
- Under Hosted sign-up and sign-in pages, click Identity providers, then select the identity provider that you configured in the previous step.
- Click Save changes.
You'll need the name of the IDP (as configured under Sign-in experience) to complete the setup of your account. Include this along with the CloudFormation outputs information shared with Zendesk.