Advanced encryption allows your company to encrypt your Service Data using your own enterprise Key Management Service (KMS), ensuring data stored in Zendesk can’t be read in plaintext by an external party and is decrypted just in time to enable Zendesk services. This feature strengthens your security posture and helps you comply with data protection and privacy obligations. See About advanced encryption to learn more.
This article helps you set up advanced encryption in your Zendesk account:
Supported Key Management Services
Before you begin, you must have a KMS in place that is supported by Zendesk for advanced encryption:
Step 1: Request access to advanced encryption
Start the setup process by requesting access to advanced encryption. Ensure the ADPP add-on is turned on in your account.
To request access to advanced encryption
- In Admin Center, click
 Account in the sidebar, then select Security > Advanced encryption.
Account in the sidebar, then select Security > Advanced encryption. - Click Request access in the lower right.

After a few moments, you'll receive an invitation email.

- Click Get Started in the email message.
A page opens, prompting you to create an account in the Secure Configuration Portal. Continue to Step 2.
You have seven days from receiving the invitation email before it expires. Click Resend email request to receive a new email if the previous invitation has expired.

Step 2: Create a Secure Configuration Portal account
Create an account in the Secure Configuration Portal to manage your KMS configurations.
To create a Secure Configuration Portal account
- After clicking Get Started in the invitation email, an account creation page appears. Create your account credentials, then click Create account.
If you manage multiple accounts, including sandboxes, choose a descriptive company name and domain to uniquely identify the account.
- Enter your name, email address, and create a password for your account.
- For Company Name, enter your Zendesk subdomain.
- For Company Domain, enter
yoursubdomain.zendesk.com, where yoursubdomain is your Zendesk subdomain. If you're testing on a sandbox first,add the sandbox subdomain.

- Your account recovery token displays. Click Download to download the token. It's important to store the token in a safe location, such as a password manager. If you forget your password, you'll be prompted to use this token.

- Click Confirm and close.
A login page appears.
- Enter the email and password you just created, then click Login.

Step 3: Configure KMS access keys
Create encryption keys in your KMS
In your Zendesk-supported KMS, create your encryption keys by following the KMS-specific instructions.
After creating encryption keys in your KMS, make a backup copy. It's important to back up your encryption keys for business continuity and disaster recovery. Zendesk won't have access to your KMS and can't assist with disaster recovery. See the documentation for your KMS for instructions.
Add your KMS configuration in the Secure Configuration Portal
Next, add your KMS credentials in the Secure Configuration Portal and configure which key to use when encrypting your data.
To add your KMS configuration
- Go to https://advanced-encryption.zendesk.com and log in to the Secure Configuration Portal.
- On the Secure Configuration Portal dashboard, click the icon for your KMS under Add Config.

- Add your access credentials and configure the key to use when encrypting your data. The steps to do this depend on which KMS you are using. Click NEED HELP? to open a step-by-step guide for your KMS.

- After you finish adding your access credentials, click Encrypt and save.
- Click Yes to set the new configuration as the primary configuration.
- The configuration is displayed on the KMS Configurations page. Note the KMS Config ID. You’ll need this ID for the next step.
 Note: Key leasing is turned on by default, which reduces the cost of using the KMS and request latency. Key leasing is an extra layer of key wrapping so the advanced encryption service doesn’t need to make a request to your KMS on every key wrap and unwrap operation. Instead, it leases a key, wrapping it using your KMS, and it uses that key for a period of time to wrap and unwrap the keys that encrypt application data. The key is checked for validity with the KMS every 10 minutes. If the key is no longer valid, it’s destroyed.
Note: Key leasing is turned on by default, which reduces the cost of using the KMS and request latency. Key leasing is an extra layer of key wrapping so the advanced encryption service doesn’t need to make a request to your KMS on every key wrap and unwrap operation. Instead, it leases a key, wrapping it using your KMS, and it uses that key for a period of time to wrap and unwrap the keys that encrypt application data. The key is checked for validity with the KMS every 10 minutes. If the key is no longer valid, it’s destroyed.
Create the KMS configuration assignment
Create the KMS configuration assignment, which allows Zendesk to use the KMS configuration to protect your data. If you added multiple KMS configurations, you must create an assignment for each.
To create the KMS configuration assignment
- In the Secure Configuration Portal, click KMS Config Assignments in the left pane.
- Click the plus icon (
 ) to add a config assignment.
) to add a config assignment.

- Complete the following fields on the Assign KMS Configuration page:
- Organization: Enter the Zendesk subdomain you're setting up for advanced encryption.
For example, if your support address is support@mondocam.zendesk.com, enter mondocam. - KMS Config ID: Enter the KMS config ID that was created after you added the KMS configuration.

- Organization: Enter the Zendesk subdomain you're setting up for advanced encryption.
- Click Save.
Step 4: Activate advanced encryption
The last step in the setup process is to activate advanced encryption.
To activate advanced encryption
- In Admin Center, click
 Account in the sidebar, then select Security > Advanced encryption.
Account in the sidebar, then select Security > Advanced encryption. - Click Next.

- Select each checkbox to confirm you understand what will happen when you activate advanced encryption.
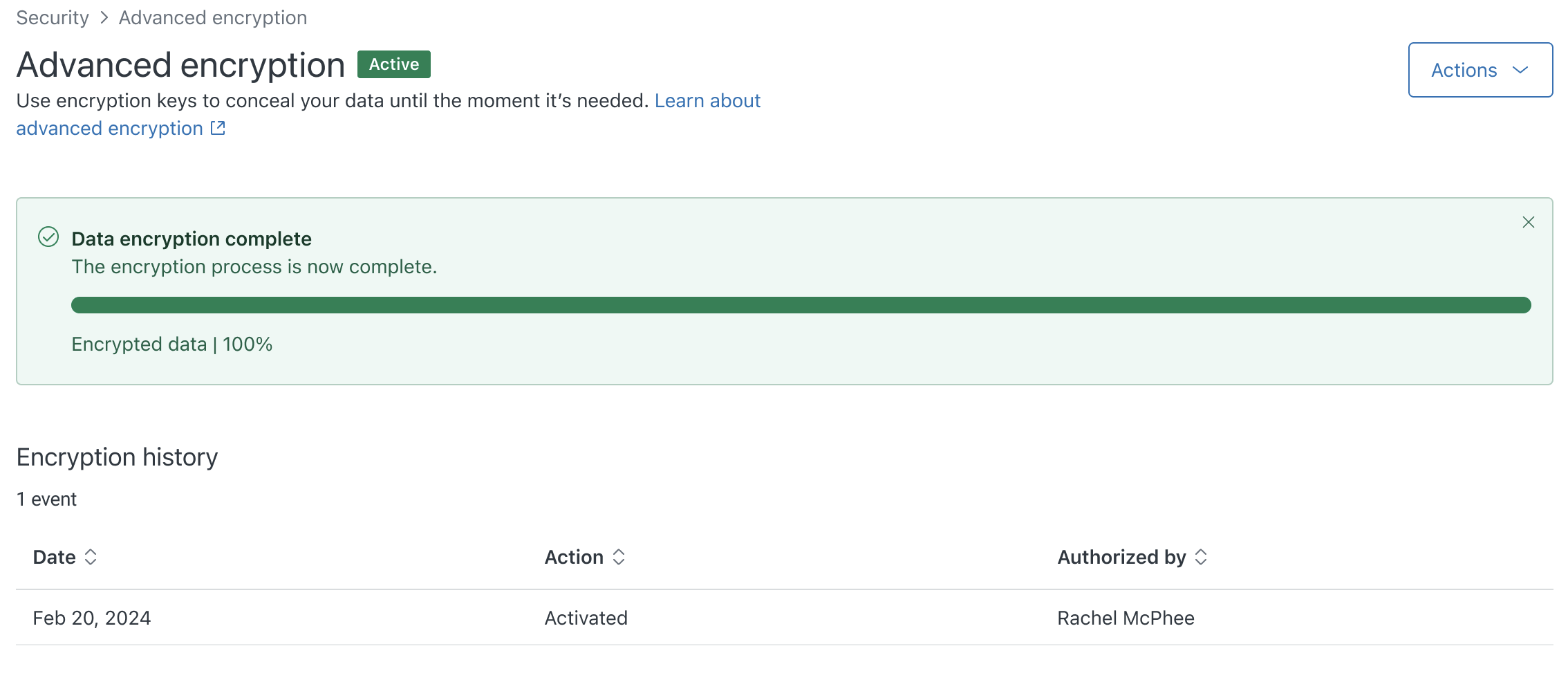
After all checkboxes are selected, the Activate encryption button becomes active.

- Click Activate encryption.
A progress bar displays the status of the data encryption process. The progress bar appears green when complete, and an Activated entry appears in the Encryption history table.