Verified AI summary ◀▼
Use the access log to monitor agent activity and enhance data security with the Advanced Data Privacy and Protection add-on. Track which tickets, user profiles, and searches agents access within the last 90 days. Filter data to refine search results and export logs using the API. This tool helps you detect security risks and ensure compliance, providing valuable insights into agent interactions.
The access log, part of the Advanced Data Privacy and Protection add-on, is a powerful tool that enhances data security and administrative control of your account. It's a record of access events for your account related to tickets, user profiles, and searches. This differs from the audit log, which provides a detailed log of changes to settings or fields.
The access log is currently available as an API and in Admin Center, and captures what data an agent or admin has accessed in your account within the last 90 days. It doesn't capture end-user activity.
Access logs can help you answer the following questions:
- What tickets are agents accessing?
- What information are agents searching for?
- What user profiles are agents viewing?
Admins and agents with permission can view the access log. See Access logs use cases and workflows for examples of how to use the access log to detect security risks and help ensure compliance.
Turning on the access log
Before you can view access logs, you must turn on the Access Log API in Admin Center. When you do, Zendesk begins capturing access events. Access events that occurred before you turned on the API aren't captured.
Only admins can turn on the access log. After you turn it on, data may take up to 60 minutes to populate.
To turn on the access log
- In Admin Center, click
 Account in the sidebar, then select Logs > Access log.
Account in the sidebar, then select Logs > Access log. - Select Turn on the Access Log API.
- Click Save.
Viewing the access log in Admin Center
The Access log page in Admin Center lets you view a detailed list of access events in your account. You must first turn on the access log before viewing it in Admin Center.
-
In Admin Center, click
 Account in the sidebar, then select Logs > Access log.
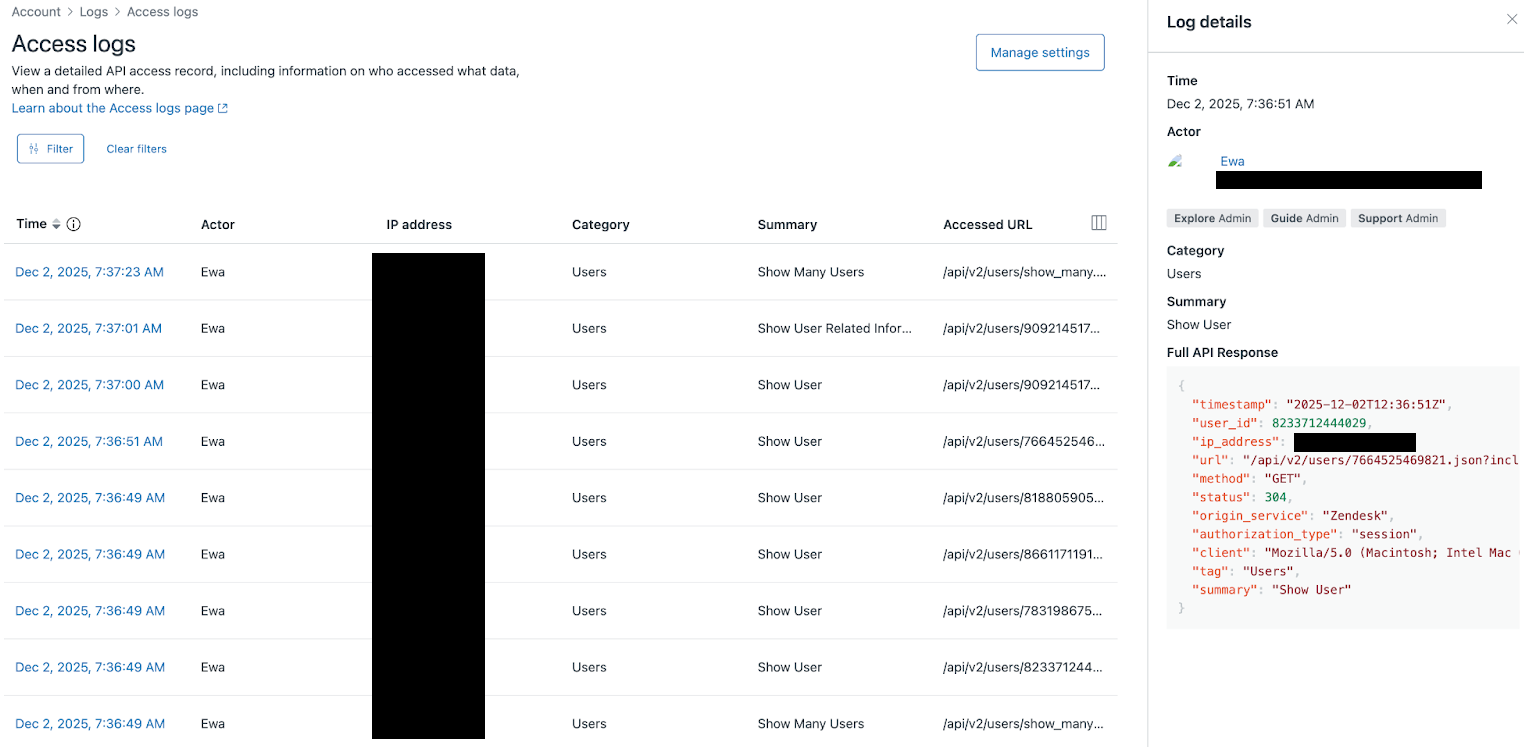
Account in the sidebar, then select Logs > Access log.The Access log page appears. Each row in the access log represents a single access event by an agent or admin in your Zendesk account. Log entries are sorted by time (newest entry first). Click an event to display its details in the right panel.
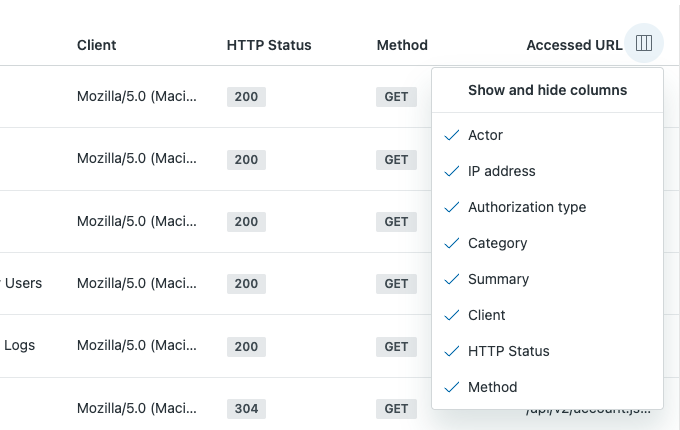
Use the Show and hide columns menu icon (![]() ) in the upper-right corner of the
table to adjust the columns that are visible in the log.
) in the upper-right corner of the
table to adjust the columns that are visible in the log.
The following information appears for each event in the access log.
| Column | Description |
|---|---|
| Time | The time and date when the page or record was accessed, displayed in your account's time zone. If you're unsure what time the access log is using, hover over the information icon in the Time column heading. |
| Actor | The team member or user who accessed the page or record in Zendesk. This helps track which users are interacting with a specific account. |
| IP address | The IP address of the user who made the request. |
| Authorization type | The method used for user authorization. Examples: Basic, Session, Digest, Bearer |
| Client | The client software that is initiating the request. Example: a web browser |
| Category | The type or classification of access that occurred, such as
Users, Profiles API, or Phone numbers. This helps identify the
function or system component involved. Some access events don't have an associated category, so this field may be empty. |
| Summary | A brief and easy-to-understand description of the access event,
such as Show user, Get profile by identifier, or List phone numbers.
Summarizes the purpose of the access entry. Some access events don't have an associated summary, so this field may be empty. |
| HTTP Status | The HTTP status code of the response. |
| Method | The HTTP method of the request. Possible values are GET, POST, PUT, and DELETE. |
| Accessed URL | The API endpoint path of the request. |
Filtering access log data to refine search results
Since the access log can include a large volume of events, filtering makes it easier to find what you’re looking for.
To filter the access log
- In Admin Center, click
 Account in the sidebar, then select Logs > Access log.
Account in the sidebar, then select Logs > Access log. - Click Filter.
Filters appear in a panel.
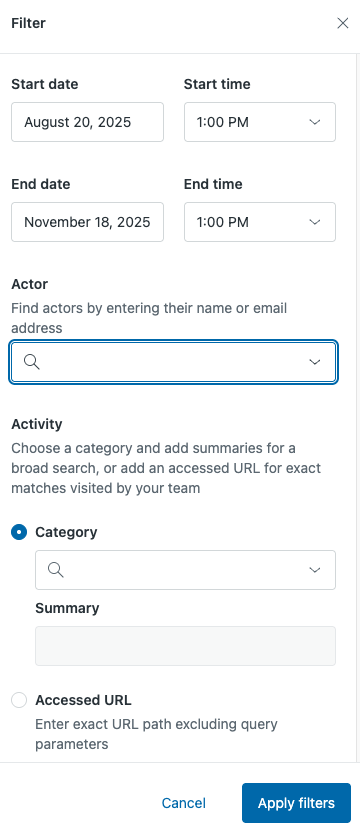
- To filter by date, set the fields Start date, Start time, End
date, and End time.
The default date reflects the maximum number of days the log can capture data (90 days). The time reflects the local time for your account in your localization settings.
- Enter a name or email address in the Actor field to filter by the people or systems responsible for the access events.
- Apply an activity filter for a more refined search:
-
Category: Type or select a category to filter events by type
(such as Users, Permissions, or Tickets). The drop-down shows a limited
number of categories and displays suggestions after typing three
characters.
After you select a category, you can narrow your results by selecting one or more items from the Summary drop-down list. For example, if you selected the Users category, you can add the Show User and Update User summary items to display only those access events.
-
Accessed URL: Use this field to filter by the accessed API
endpoint path. Example:
/api/v2/users/6649960843290/related.json
-
Category: Type or select a category to filter events by type
(such as Users, Permissions, or Tickets). The drop-down shows a limited
number of categories and displays suggestions after typing three
characters.
- Click Apply filters.
Using the API to export access logs
Use the Access Logs API to export access logs to a CSV file. The API lets you filter the logs using the same filters as the Admin Center user interface, as described in Filtering the data to refine search results. You can also use scripting to filter the returned data.
You’ll need to work with a developer or other technical resource at your company to export the data. See Exporting access logs to a CSV file and Zendesk API Reference: Access Logs.